This article has multiple issues. Please help improve it or discuss these issues on the talk page. (Learn how and when to remove these messages)
|
In computer security, organization-based access control (OrBAC) is an access control model first presented in 2003. The current approaches of the access control rest on the three entities (subject, action, object) to control the access the policy specifies that some subject has the permission to realize some action on some object.
OrBAC allows the policy designer to define a security policy independently of the implementation. The chosen method to fulfill this goal is the introduction of an abstract level.
- Subjects are abstracted into roles. A role is a set of subjects to which the same security rule apply.
- Similarly, an activity is a set of actions to which the same security rule apply.
- And, a view is a set of objects to which the same security rule apply.
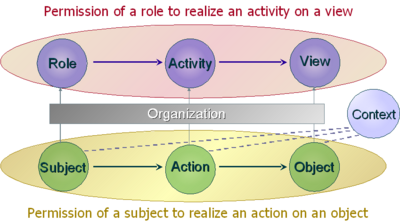
Each security policy is defined for and by an organization. Thus, the specification of the security policy is completely parameterized by the organization so that it is possible to handle simultaneously several security policies associated with different organizations. The model is not restricted to permissions, but also includes the possibility to specify prohibitions and obligations. From the three abstract entities (roles, activities, views), abstract privileges are defined. And from these abstract privileges, concrete privileges are derived.
OrBAC is context sensitive, so the policy could be expressed dynamically. Furthermore, OrBAC owns concepts of hierarchy (organization, role, activity, view, context) and separation constraints.
See also
- Access control list
- Attribute-Based Access Control (ABAC)
- Context-based access control (CBAC)
- Discretionary access control (DAC)
- Graph-based access control (GBAC)
- Lattice-based access control (LBAC)
- Mandatory access control (MAC)
- Role-based access control (RBAC)
- Rule-set-based access control (RSBAC)
- Capability-based security
- Risk-based authentication
- Bell–LaPadula model