QARMA (from Qualcomm ARM Authenticator) is a lightweight tweakable block cipher primarily known for its use in the ARMv8 architecture for protection of software as a cryptographic hash for the Pointer Authentication Code. The cipher was proposed by Roberto Avanzi in 2016. Two versions of QARMA are defined: QARMA-64 (64-bit block size with a 128-bit encryption key) and QARMA-128 (128-bit block size with a 256-bit key). The design of the QARMA was influenced by PRINCE and MANTIS. The cipher is intended for fully-unrolled hardware implementations with low latency (like memory encryption). Unlike the XTS mode, the address can be directly used as a tweak and does not need to be whitened with the block encryption first.
Architecture
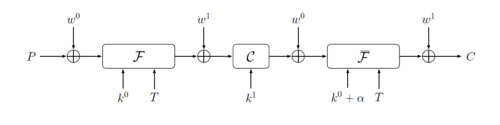
QARMA is an Even–Mansour cipher using three stages, with whitening keys w and w XORed in between:
- permutation F is using core key k and parameterized by a tweak T. It has r rounds inside (r = 7 for QARMA-64, r = 11 for QARMA-128);
- "central" permutation C is using key k and is designed to be reversible via a simple key transformation (contains two central rounds);
- the third permutation is an inverse of the first (r more rounds).
All keys are derived from the master encryption key K using specialisation:
- K is partitioned into halves as w Concatenation k, each will have halfsize bits;
- for encryption w = (w >>> 1) + (w >> (halfsize-1));
- for encryption k = k;
- for decryption, the same design can be used as long as k+α is used as a core key, k = Q•k, w and w are swapped. α here is a special constant and Q a special involutary matrix. This construct is similar to the alpha reflection in PRINCE.
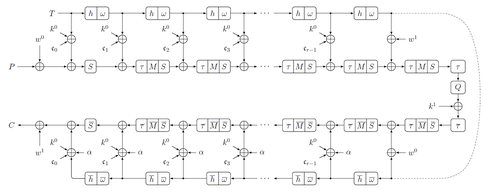
The data is split into 16 cells (4-bit nibbles for QARMA-64, 8-bit bytes for QARMA-128). Internal state also contains 16 cells, arranged in a 4x4 matrix, and is initialized by plaintext (XORed with w). In each round of , the state is transformed via operations :
- is ShuffleCells, a MIDORI permutation of cells ();
- is MixColumns: each column is multiplied by a fixed matrix M;
- is SubCells: each cell is transformed using an S-box.
The tweak for each round is updated using :
- is a cell permutation from MANTIS ();
- is an LFSR applied to each of the cells with numbers . For QARMA-64, the LFSR is (b3, b2, b1, b0) ⇒ (b0 + b1, b3, b2, b1), for QARMA-128, (b7, b6, ..., b0) ⇒ (b0 + b2, b7, b6, ..., b1),
The rounds of consist of inverse operations . Central rounds, in addition to two rounds ( and ), include multiplication of the state by an involutary matrix Q.
References
- Qameleon v. 1.0: A Submission to the NIST Lightweight Cryptography Standardization Process
- ^ Zong & Dong 2016.
- ^ Avanzi 2016.
Sources
- Avanzi, Roberto (2016). The QARMA Block Cipher Family (PDF). IACR Transactions on Symmetric Cryptology (ToSC). Vol. 17 (published 8 March 2017). pp. 4–44. doi:10.13154/tosc.v2017.i1.4-44. Archived from the original (PDF) on May 13, 2020.
- Zong, Rui; Dong, Xiaoyang (2016). "Meet-in-the-Middle Attack on QARMA Block Cipher" (PDF). iacr.org. IACR. Retrieved 10 June 2022.
- Kaur, Jasmin; Kermani, Mehran Mozaffari; Azarderakhsh, Reza (1 January 2022). "Hardware Constructions for Lightweight Cryptographic Block Cipher QARMA With Error Detection Mechanisms". IEEE Transactions on Emerging Topics in Computing. 10 (1): 514–519. doi:10.1109/TETC.2020.3027789. eISSN 2376-4562. S2CID 226665710.
- Li, Rongjia; Jin, Chenhui (4 May 2018). "Meet-in-the-Middle Attacks on Reduced-Round QARMA-64/128". The Computer Journal. 61 (8): 1158–1165. doi:10.1093/comjnl/bxy045. eISSN 1460-2067. ISSN 0010-4620.
- Yang, Dong; Qi, Wen-feng; Chen, Hua-jin (2018). "Impossible Differential Attack on QARMA Family of Block Ciphers". Cryptology ePrint Archive.
External links
- Public-domain Python implementation of QARMA-64
- Open-source (MIT license) implementation of QARMA-64 in C
 are at the top, rounds of
are at the top, rounds of  are at the bottom,
are at the bottom,  is on the right. Inner path describes the transformation of the internal state, outer path corresponds to the tweak update. ci are
is on the right. Inner path describes the transformation of the internal state, outer path corresponds to the tweak update. ci are  :
:
 is ShuffleCells, a
is ShuffleCells, a  is MixColumns: each column is multiplied by a fixed matrix M;
is MixColumns: each column is multiplied by a fixed matrix M; is SubCells: each cell is transformed using an
is SubCells: each cell is transformed using an  :
:
 is a cell permutation from MANTIS ();
is a cell permutation from MANTIS (); is an
is an  .
Central rounds, in addition to two rounds (
.
Central rounds, in addition to two rounds ( ), include multiplication of the state by an involutary matrix Q.
), include multiplication of the state by an involutary matrix Q.