| Revision as of 09:34, 8 February 2011 edit213.103.192.37 (talk) →Other representations: Improve alignment of the ascii representation.← Previous edit | Revision as of 14:31, 8 February 2011 edit undoAnonMoos (talk | contribs)Autopatrolled, Extended confirmed users, Pending changes reviewers71,937 edits cutting down tag-bombing to essentialsNext edit → | ||
| Line 2: | Line 2: | ||
| {{COI|date=February 2011}} | {{COI|date=February 2011}} | ||
| {{Peacock|date=February 2011}} | {{Peacock|date=February 2011}} | ||
| {{Unreliable sources|date=February 2011}} | |||
| {{Self-published|date=February 2011}} | {{Self-published|date=February 2011}} | ||
Revision as of 14:31, 8 February 2011
| The topic of this article may not meet Misplaced Pages's general notability guideline. Please help to demonstrate the notability of the topic by citing reliable secondary sources that are independent of the topic and provide significant coverage of it beyond a mere trivial mention. If notability cannot be shown, the article is likely to be merged, redirected, or deleted. Find sources: "Hacker Emblem" – news · newspapers · books · scholar · JSTOR (February 2011) (Learn how and when to remove this message) |
| A major contributor to this article appears to have a close connection with its subject. It may require cleanup to comply with Misplaced Pages's content policies, particularly neutral point of view. Please discuss further on the talk page. (February 2011) (Learn how and when to remove this message) |
| This article contains wording that promotes the subject in a subjective manner without imparting real information. Please remove or replace such wording and instead of making proclamations about a subject's importance, use facts and attribution to demonstrate that importance. (February 2011) (Learn how and when to remove this message) |
| This article may contain excessive or inappropriate references to self-published sources. Please help improve it by removing references to unreliable sources where they are used inappropriately. (February 2011) (Learn how and when to remove this message) |
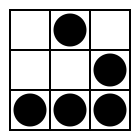
The Hacker Emblem was first proposed in October 2003 by Eric S. Raymond, who claimed a need for a unifying and recognizable symbol for his perception of hacker culture. This does not refer to the hackers breaking into computers, but to the hacker culture around BSD, MIT, GNU, Linux, Perl, etc.; that is, the community around free software and open source.
Raymond has said that one does not claim to be a hacker by displaying this emblem, but suggests that "by using this emblem, you express sympathy with hackers' goals, hackers' values, and the hacker way of living".
The image itself is a representation of a glider formation in Conway's Game of Life.
Hackers also associate and represent themselves with mascots from notable free and open source projects such as the GNU Project's "Gnu" or more commonly the Linux kernel's "Tux". The "Dust Puppy" from the web comic User Friendly is also commonly associated with Hackers, Internet culture, and free and open source communities due to the strip's coverage of those topics.

Other representations
Other means to display the image have evolved, mostly relying on ASCII art. Examples include:
|_|0|_| 0 1 0 . o . |_|_|0| 0 0 1 . . o |0|0|0| 1 1 1 o o o
Minimal ASCII representation
On February 12, 2008, the minimal ASCII representation was incorporated into Raymond's list of canonical representations:
. ..:
Minimal UTF-8 representation
This article contains special characters. Without proper rendering support, you may see question marks, boxes, or other symbols.Braille characters present in the UTF-8 charset can also be used to produce a single-line representation:
⠠⠵
See also
References
- the Hacker Emblem page on Eric S. Raymond's site
- Raymond, Eric (2008-02-12). "Re: Hacker Emblem". Retrieved 2008-02-13.
{{cite web}}: Unknown parameter|coauthors=ignored (|author=suggested) (help)
External links
- The Glider: Proposal for a Hacker Emblem Contains more information on the Hacker Emblem proposal, including SVG and TeX sources and FAQs.
- "How To Become a Hacker" A document explaining the hacker culture.
| Conway's Game of Life and related cellular automata | |
|---|---|
| Structures | |
| Life variants | |
| Concepts | |
| Implementations | |
| Key people | |
| Websites | |
| Popular culture | |