| Revision as of 20:41, 24 October 2014 edit128.163.7.150 (talk) →Bytecode interpreter and just-in-time compiler← Previous edit | Revision as of 01:38, 26 October 2014 edit undo39.32.244.145 (talk) →Bytecode verifierNext edit → | ||
| Line 78: | Line 78: | ||
| The verifier permits only some bytecode sequences in valid programs, e.g. a ] can only target an instruction within the same ]. Furthermore, the verifier ensures that any given instruction operates on a fixed stack location,<ref>{{cite web |title=The Verification process |url=http://java.sun.com/docs/books/jvms/second_edition/html/ClassFile.doc.html#9766 |work=The Java Virtual Machine Specification |publisher=Sun Microsystems |year=1999 |accessdate=2009-05-31}}</ref> allowing the JIT compiler to transform stack accesses into fixed register accesses. Because of this, that the JVM is a stack architecture does not imply a speed penalty for emulation on ] when using a JIT compiler. In the face of the code-verified JVM architecture, it makes no difference to a JIT compiler whether it gets named imaginary registers or imaginary stack positions that must be allocated to the target architecture's registers. In fact, code verification makes the JVM different from a classic stack architecture, of which efficient emulation with a JIT compiler is more complicated and typically carried out by a slower interpreter. | The verifier permits only some bytecode sequences in valid programs, e.g. a ] can only target an instruction within the same ]. Furthermore, the verifier ensures that any given instruction operates on a fixed stack location,<ref>{{cite web |title=The Verification process |url=http://java.sun.com/docs/books/jvms/second_edition/html/ClassFile.doc.html#9766 |work=The Java Virtual Machine Specification |publisher=Sun Microsystems |year=1999 |accessdate=2009-05-31}}</ref> allowing the JIT compiler to transform stack accesses into fixed register accesses. Because of this, that the JVM is a stack architecture does not imply a speed penalty for emulation on ] when using a JIT compiler. In the face of the code-verified JVM architecture, it makes no difference to a JIT compiler whether it gets named imaginary registers or imaginary stack positions that must be allocated to the target architecture's registers. In fact, code verification makes the JVM different from a classic stack architecture, of which efficient emulation with a JIT compiler is more complicated and typically carried out by a slower interpreter. | ||
| Code verification also ensures that arbitrary bit patterns cannot get used as an address. ] is achieved without the need for a ] (MMU). Thus, JVM is an efficient way to get memory protection on simple architectures that lack an MMU. This is analogous to ] in Microsoft's .NET ], and conceptually similar to ]s such as the ], and IBM ]. | |||
| The original specification for the bytecode verifier used natural language that was ''incomplete or incorrect in some respects.'' A number of attempts have been made to specify the JVM as a formal system. By doing this, the security of current JVM implementations can more thoroughly be analyzed, and potential security exploits prevented. It will also be possible to optimize the JVM by skipping unnecessary safety checks, if the application being run is proven to be safe.<ref>Stephen N. Freund and John C. Mitchell. 1999. A formal framework for the Java bytecode language and verifier. In Proceedings of the 14th ACM SIGPLAN conference on Object-oriented programming, systems, languages, and applications (OOPSLA '99), A. Michael Berman (Ed.). ACM, New York, NY, USA, 147–166. DOI=10.1145/320384.320397 http://doi.acm.org/10.1145/320384.320397</ref> | The original specification for the bytecode verifier used natural language that was ''incomplete or incorrect in some respects.'' A number of attempts have been made to specify the JVM as a formal system. By doing this, the security of current JVM implementations can more thoroughly be analyzed, and potential security exploits prevented. It will also be possible to optimize the JVM by skipping unnecessary safety checks, if the application being run is proven to be safe.<ref>Stephen N. Freund and John C. Mitchell. 1999. A formal framework for the Java bytecode language and verifier. In Proceedings of the 14th ACM SIGPLAN conference on Object-oriented programming, systems, languages, and applications (OOPSLA '99), A. Michael Berman (Ed.). ACM, New York, NY, USA, 147–166. DOI=10.1145/320384.320397 http://doi.acm.org/10.1145/320384.320397</ref> | ||
Revision as of 01:38, 26 October 2014
"JRE" redirects here. For the podcast, see Joe Rogan Experience.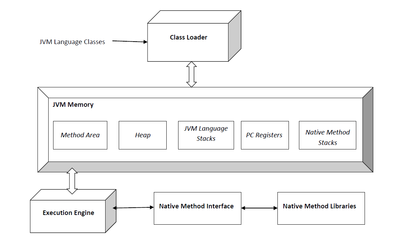
A Java virtual machine (JVM) is an abstract computing machine. There are three notions of the JVM: specification, implementation, and instance. An instance of the JVM can execute any executable computer program compiled into Java bytecode. It is the code execution component of the Java platform.
Overview
The Java virtual machine is called "virtual" because it is an abstract computer defined by a specification. JVM specification omits implementation details that are not part of the Java virtual machine's specification. For example, the memory layout of run-time data areas, the garbage-collection algorithm used, and any internal optimization of the Java virtual machine instructions (their translation into machine code). The main reason for this omission is to not unnecessarily constrain the creativity of implementors. Any Java application can be run only inside a run-time instance of some concrete implementation of the abstract specification of the Java virtual machine
JVM languages
|
|
JVM Language is any language with functionality that can be expressed in terms of a valid class file which can be hosted by the Java Virtual Machine. A class file contains Java Virtual Machine instructions (or bytecodes ) and a symbol table, as well as other ancillary information. The class file format, the hardware- and operating system- independent binary format used to represent compiled classes and interfaces. Java 7 JVM implements JSR 292: Supporting Dynamically Typed Languages on the Java Platform, a new feature which supports dynamically typed languages in the JVM.This feature is developed within the Da Vinci Machine Project which mission is to extend the JVM so that it supports languages other than Java.
Bytecode verifier
A basic philosophy of Java is that it is inherently safe from the standpoint that no user program can crash the host machine or otherwise interfere inappropriately with other operations on the host machine, and that it is possible to protect certain methods and data structures belonging to trusted code from access or corruption by untrusted code executing within the same JVM. Furthermore, common programmer errors that often lead to data corruption or unpredictable behavior such as accessing off the end of an array or using an uninitialized pointer are not allowed to occur. Several features of Java combine to provide this safety, including the class model, the garbage-collected heap, and the verifier.
The JVM verifies all bytecode before it is executed. This verification consists primarily of three types of checks:
- Branches are always to valid locations
- Data is always initialized and references are always type-safe
- Access to private or package private data and methods is rigidly controlled
The first two of these checks take place primarily during the verification step that occurs when a class is loaded and made eligible for use. The third is primarily performed dynamically, when data items or methods of a class are first accessed by another class.
The verifier permits only some bytecode sequences in valid programs, e.g. a jump (branch) instruction can only target an instruction within the same method. Furthermore, the verifier ensures that any given instruction operates on a fixed stack location, allowing the JIT compiler to transform stack accesses into fixed register accesses. Because of this, that the JVM is a stack architecture does not imply a speed penalty for emulation on register-based architectures when using a JIT compiler. In the face of the code-verified JVM architecture, it makes no difference to a JIT compiler whether it gets named imaginary registers or imaginary stack positions that must be allocated to the target architecture's registers. In fact, code verification makes the JVM different from a classic stack architecture, of which efficient emulation with a JIT compiler is more complicated and typically carried out by a slower interpreter.
The original specification for the bytecode verifier used natural language that was incomplete or incorrect in some respects. A number of attempts have been made to specify the JVM as a formal system. By doing this, the security of current JVM implementations can more thoroughly be analyzed, and potential security exploits prevented. It will also be possible to optimize the JVM by skipping unnecessary safety checks, if the application being run is proven to be safe.
Bytecode instructions
Main article: Java bytecodeThe JVM has instructions for the following groups of tasks:
- Load and store
- Arithmetic
- Type conversion
- Object creation and manipulation
- Operand stack management (push / pop)
- Control transfer (branching)
- Method invocation and return
- Throwing exceptions
- Monitor-based concurrency
The aim is binary compatibility. Each particular host operating system needs its own implementation of the JVM and runtime. These JVMs interpret the bytecode semantically the same way, but the actual implementation may be different. More complex than just emulating bytecode is compatibly and efficiently implementing the Java core API that must be mapped to each host operating system.
Heap
The Java virtual machine heap is the area of memory used by the JVM, specifically HotSpot, for dynamic memory allocation. The heap is divided into generations:
- The young generation stores short-lived objects that are created and immediately garbage collected.
- Objects that persist longer are moved to the old generation (also called the tenured generation).
The permanent generation (or permgen) was used for class definitions and associated metadata prior to Java 8. Permanent generation was not part of the heap. The permanent generation was removed from Java 8.
Originally there was no permanent generation, and objects and classes were stored together in the same area. But as class unloading occurs much more rarely than objects are collected, moving class structures to a specific area allowed significant performance improvements.
Secure execution of remote code
A virtual machine architecture allows very fine-grained control over the actions that code within the machine is permitted to take. This is designed to allow safe execution of untrusted code from remote sources, a model used by Java applets. Applets run within a VM incorporated into a user's browser, executing code downloaded from a remote HTTP server. The remote code runs in a restricted sandbox, which is designed to protect the user from misbehaving or malicious code. Publishers can purchase a certificate with which to digitally sign applets as safe, giving them permission to ask the user to break out of the sandbox and access the local file system, clipboard, execute external pieces of software, or network.
Bytecode interpreter and just-in-time compiler
If the Java Virtual Machine is an abstract computer then its machine language is the Java bytecode. For each type of real computer a different Java bytecode interpreter is needed. When a computer has a Java bytecode interpreter, it can run any Java bytecode program, and the same program can be run on any computer that has such an interpreter.
There are two basic reasons for having the Java bytecode interpreter:
Simplicity: The Java compiler is itself a complex program. A Java bytecode interpreter, is a relatively small, simple program. This makes it easy to write a bytecode interpreter for a new type of computer; once that is done, that computer can run any compiled Java program. It would be much harder to write a Java compiler for the same computer.
Security: The bytecode interpreter is a buffer between the user and the program the user downloads. The user is really running the interpreter, which runs the downloaded program indirectly. The interpreter can protect the user from potentially dangerous actions on the part of that program.
Since Java bytecode was executed by an interpreter, the execution will be always slower than the execution of the same program compiled into native machine language. This problem was resolved by introducing just-in-time (JIT) compilers for executing Java bytecode. A just-in-time compiler translates Java bytecode into native machine language. It does this while it is executing the program. The input to a just-in-time compiler is a Java bytecode program, and its task is to execute that program.
While it is executing the program, it also translates parts of the program into machine language of the underlying computer. The translated parts of the program can then be executed much more quickly than they could be interpreted. This technique gets applied to those parts of a program frequently executed. This way a just-in-time compiler can significantly speed up the overall execution time.
There is no necessary connection between Java and Java bytecode. A program written in Java can be compiled into the machine language of a real computer. And programs written in other languages can be compiled into Java bytecode, too. The combination of Java and Java bytecode is platform-independent, secure, and network-compatible while allowing the user to program in a modern high-level object-oriented language.
Some JVM implementations do not include an interpreter which way the just-in-time compilation of the byte code into native machine code has to occur before a method executes. The JIT compilation is performed the first time a Java method is called.
Licensing
Starting with Java Platform, Standard Edition (J2SE) 5.0, changes to the JVM specification have been developed under the Java Community Process as JSR 924. As of 2006, changes to specification to support changes proposed to the class file format (JSR 202) are being done as a maintenance release of JSR 924. The specification for the JVM is published in book form, known as blue book. The preface states:
We intend that this specification should sufficiently document the Java Virtual Machine to make possible compatible clean-room implementations. Oracle provides tests that verify the proper operation of implementations of the Java Virtual Machine.
One of Oracle's JVMs is named HotSpot. Clean-room Java implementations include Kaffe and IBM J9. Oracle retains control over the Java trademark, which it uses to certify implementation suites as fully compatible with Oracle's specification.
See also
- List of Java virtual machines
- Comparison of Java virtual machines
- Comparison of application virtual machines
- Automated exception handling
- Java performance
- List of JVM languages
- Java processor
- Common Language Runtime
Notes
- Inside the Java Virtual Machine by Bill Venners, Chapter 5 http://www.artima.com/insidejvm/ed2/index.html
- 1996, possibly the first new language specifically designed to run on the JVM)
- The Java® Virtual Machine Specification Java SE 7 Edition http://docs.oracle.com/javase/specs/jvms/se7/jvms7.pdf
- New JDK 7 Feature: Support for Dynamically Typed Languages in the Java Virtual Machine http://www.oracle.com/technetwork/articles/javase/dyntypelang-142348.html
- "The Verification process". The Java Virtual Machine Specification. Sun Microsystems. 1999. Retrieved 2009-05-31.
- Stephen N. Freund and John C. Mitchell. 1999. A formal framework for the Java bytecode language and verifier. In Proceedings of the 14th ACM SIGPLAN conference on Object-oriented programming, systems, languages, and applications (OOPSLA '99), A. Michael Berman (Ed.). ACM, New York, NY, USA, 147–166. DOI=10.1145/320384.320397 http://doi.acm.org/10.1145/320384.320397
- "Frequently Asked Questions about Garbage Collection in the Hotspot Java Virtual Machine". Sun Microsystems. 6 February 2003. Retrieved 7 February 2009.
- ^ Masamitsu, Jon (28 November 2006). "Presenting the Permanent Generation". Retrieved 7 February 2009.
- Nutter, Charles (11 September 2008). "A First Taste of InvokeDynamic". Retrieved 7 February 2009.
- "JEP 122: Remove the Permanent Generation". Oracle Corporation. 2012-12-04. Retrieved 2014-03-23.
- http://math.hws.edu/javanotes/c1/s3.html Introduction to Programming Using Java, Seventh Edition, Version 7.0, August 2014 by David J. Eck Section 1.3 The Java Virtual Machine
- http://docs.oracle.com/cd/E15289_01/doc.40/e15058/underst_jit.htm Oracle® JRockit Introduction Release R28 2. Understanding Just-In-Time Compilation and Optimization
- JSR 924, specifies changes to the JVM specification starting with J2SE 5.0
- JSR 202, specifies a number of changes to the class file format
- The Java Virtual Machine Specification (the first and second editions are also available online)
References
- Clarifications and Amendments to the Java Virtual Machine Specification, Second Edition includes list of changes to be made to support J2SE 5.0 and JSR 45
- JSR 45, specifies changes to the class file format to support source-level debugging of languages such as JavaServer Pages (JSP) and SQLJ that are translated to Java
External links
- The Java Virtual Machine Specification
- Template:Dmoz
- Java Virtual Machine Download Link
- JVM implementation in pure Java
| Java virtual machines (comparison) | |
|---|---|
| Sun, Oracle | |
| Major implementations | |
| Embedded | |
| Others | |
| Discontinued | |
| Java (software platform) | |||||||
|---|---|---|---|---|---|---|---|
| Platforms |
|  | |||||
| Oracle technologies | |||||||
| Platform technologies | |||||||
| Major third-party technologies | |||||||
| History | |||||||
| JVM languages | |||||||
| Community |
| ||||||
| Sun Microsystems | ||||||||
|---|---|---|---|---|---|---|---|---|
| Acquired by Oracle | ||||||||
| Hardware |
| |||||||
| Software | ||||||||
| Storage | ||||||||
| Performance | ||||||||
| Research | ||||||||
| Education | ||||||||
| Community |
| |||||||
| Acquisitions | ||||||||
| Slogans | ||||||||
| Category | ||||||||